Difference between revisions of "SystemUpdater"
m (Proof.) |
(Fixed calling encryption signing.) |
||
| (One intermediate revision by the same user not shown) | |||
| Line 13: | Line 13: | ||
}} | }} | ||
| − | The '''SystemUpdater''' is a collection of TAD files that allow you to update an IS-TWL-DEBUGGER or DSi Panda. These were | + | The '''SystemUpdater''' is a collection of TAD files that allow you to update an IS-TWL-DEBUGGER or DSi Panda. These were only used for development consoles, and they do not work on retail units. |
==Features== | ==Features== | ||
| − | + | The cartridge contains updates for all regions (including China and Korea since v1.4) and they will be installed when selected. When a region has been selected, all the data will be deleted from the NAND and update-signed TAD's will be installed. The stage2 bootloader will also be installed if needed. Unlike regular TWL carts and exploits that do not have NAND access, this one does. If done correctly, the tickets, TWLCFG0.dat, TWLCFG1.dat and the system menu, with the bundled DSi applications have been installed. [[TwlNmenu]] and [[NandFiler]] are optional. | |
The cartridge can also detect if you're on a Panda or Debugger. If 16MB of memory is found, it will be listed as '''TWL CONSOLE''' (Panda, IS-TWL-CAPTURE). | The cartridge can also detect if you're on a Panda or Debugger. If 16MB of memory is found, it will be listed as '''TWL CONSOLE''' (Panda, IS-TWL-CAPTURE). | ||
| Line 30: | Line 30: | ||
[[File:TWLCartNonWatermark.jpg|thumb|150px|left|Confirmed image of the cartridge. The same cartridge is used for TWL prototypes and other development applications.]] | [[File:TWLCartNonWatermark.jpg|thumb|150px|left|Confirmed image of the cartridge. The same cartridge is used for TWL prototypes and other development applications.]] | ||
==Uniquely signed TADs== | ==Uniquely signed TADs== | ||
| − | The TAD files in NitroFS are not development | + | The TAD files in NitroFS are not development encryped<ref>[https://randommeaninglesscharacters.com/dsidev/twlsystemupdater.html Twl SystemUpdater (rmc)]</ref>. Rather than being created with "[https://randommeaninglesscharacters.com/dsidev/man/maketad.html maketad.exe]" like most TADs, these are created with "maketad.updater.exe" from TwlIPL. This tool encrypts the TAD contents with the debugger common key, found in the ARM7 bootrom right after the dev/prod common key. TwlNmenu does not work with debugger key, so you'll need to decrypt the TADs with [https://github.com/rvtr/remaketad.pl/ this script]. |
| + | |||
| + | The debugger common key: <code>A2FDDDF2E423574AE7ED8657B5AB19D3</code> | ||
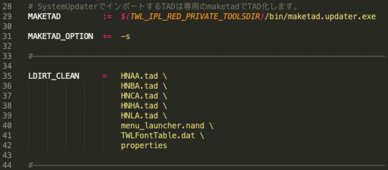
The signing process for the updater TADs can be found in the gigaleaks at: '''TwlIPL/trunk/build/systemMenu_tools/SystemUpdater/data/Makefile''' | The signing process for the updater TADs can be found in the gigaleaks at: '''TwlIPL/trunk/build/systemMenu_tools/SystemUpdater/data/Makefile''' | ||
| Line 45: | Line 47: | ||
*Holding SELECT and A at the same time when continuing an update skips the installation for TwlNmenu and NandFiler. | *Holding SELECT and A at the same time when continuing an update skips the installation for TwlNmenu and NandFiler. | ||
| − | *Instead of the version number being (eg.) v1.4E, it | + | *Instead of the version number being (eg.) v1.4E, it will be appended with "_dev", notifying you it has been updated using a SystemUpdater cartridge. |
*The development DSi firmware cannot import or export .bin files from the system settings like a retail unit. It can only delete applications, therefore, TwlNmenu must be used. | *The development DSi firmware cannot import or export .bin files from the system settings like a retail unit. It can only delete applications, therefore, TwlNmenu must be used. | ||
Latest revision as of 11:38, 23 November 2024
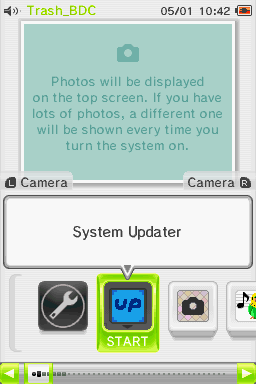 Picture of v1.4a, running on No$GBA | |
| Cart ID | NTRJ - 0SUA |
|---|---|
| Found versions | v1.3a, v1.4, v1.4a |
| ROM Build Date | 2010-04-15 (v1.4a) |
The SystemUpdater is a collection of TAD files that allow you to update an IS-TWL-DEBUGGER or DSi Panda. These were only used for development consoles, and they do not work on retail units.
Features
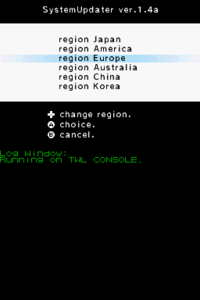
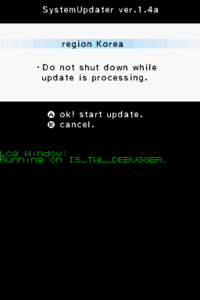
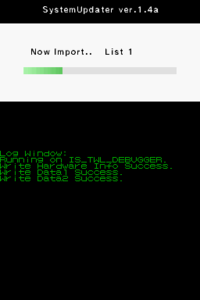
The cartridge contains updates for all regions (including China and Korea since v1.4) and they will be installed when selected. When a region has been selected, all the data will be deleted from the NAND and update-signed TAD's will be installed. The stage2 bootloader will also be installed if needed. Unlike regular TWL carts and exploits that do not have NAND access, this one does. If done correctly, the tickets, TWLCFG0.dat, TWLCFG1.dat and the system menu, with the bundled DSi applications have been installed. TwlNmenu and NandFiler are optional.
The cartridge can also detect if you're on a Panda or Debugger. If 16MB of memory is found, it will be listed as TWL CONSOLE (Panda, IS-TWL-CAPTURE). If 32MB of memory is found, it will be listed as IS_TWL_DEBUGGER.
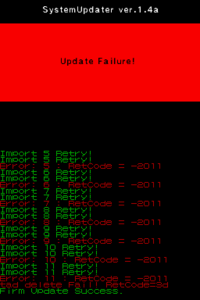
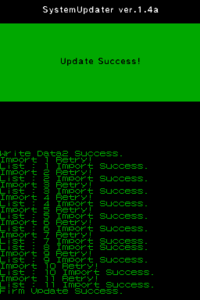
- SystemUpdater Images
Uniquely signed TADs
The TAD files in NitroFS are not development encryped[1]. Rather than being created with "maketad.exe" like most TADs, these are created with "maketad.updater.exe" from TwlIPL. This tool encrypts the TAD contents with the debugger common key, found in the ARM7 bootrom right after the dev/prod common key. TwlNmenu does not work with debugger key, so you'll need to decrypt the TADs with this script.
The debugger common key: A2FDDDF2E423574AE7ED8657B5AB19D3
The signing process for the updater TADs can be found in the gigaleaks at: TwlIPL/trunk/build/systemMenu_tools/SystemUpdater/data/Makefile
Available versions
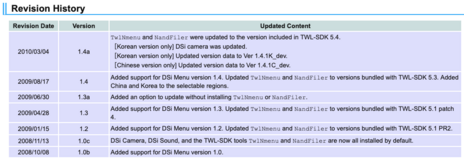
With the updater comes a HTML file for instructions and troubleshooting. On the bottom of the page is a changelog[2] listed.
References
Notes
- Holding SELECT and A at the same time when continuing an update skips the installation for TwlNmenu and NandFiler.
- Instead of the version number being (eg.) v1.4E, it will be appended with "_dev", notifying you it has been updated using a SystemUpdater cartridge.
- The development DSi firmware cannot import or export .bin files from the system settings like a retail unit. It can only delete applications, therefore, TwlNmenu must be used.