Difference between revisions of "CrashMe"
m |
|||
| Line 30: | Line 30: | ||
{|style="margin: 0 auto;" | {|style="margin: 0 auto;" | ||
| − | | [[File:Trojan-dsbrick-taihen1.png|center|thumb|Hentai... | + | | [[File:Trojan-dsbrick-taihen1.png|center|thumb|Hentai... Hot, am I right?]] |
| [[File:Trojan-dsbrick-owata1.png|center|thumb|"Owata" means "finished" in English, meaning that your DS has been "finished" off.]] | | [[File:Trojan-dsbrick-owata1.png|center|thumb|"Owata" means "finished" in English, meaning that your DS has been "finished" off.]] | ||
|} | |} | ||
Revision as of 20:08, 21 August 2019
CrashMe is a series of trojan horses developed for the Nintendo DS. Its main purpose was to attack pirates, as it will flood the Nintendo DS firmware with junk data, rendering it unusable.
Contents
Origin
The origin of these trojans started back in 2005 with the PlayStation Portable, known as a trojan simply known as Trojan.PSPBrick. The trojan was hidden as a "version downgrader", as it would delete critical files that would restart the PSP, and replace those files with the following messages:
Your 2.0 is hacked please reboot Thank you PSP Team the french team FuCk yoshihiro and SonyxTeam Looser
PSP TEAM 2.0 Exploit Hack the 2.0 firmware Thank's to toc2rta for the 2.0 exploit
Trying to open any application after that would simply freeze the unit, with little to no recovery being possible. This trojan is what inspired DarkFader, to create a version for the Nintendo DS, with similarities shown.
Trojan.DSBrick.B (taihen.zip)
On October 8th 2005, just a few days from the discovery of Trojan.PSPBrick, DarkFader privately released a trojan for the Nintendo DS on IRC, which later made its way onto people's DS'es. The link pretended it was a XS4All link, a Dutch internet provider, and the trojan came in an archive known as taihen.zip. The only contents were taihen.nds and taihen.txt with some text.
This is a small hentai slideshow for the Nintendo DS. Enjoy!
The program was disguised as a hentai viewer which would show 5 images of uncensored hentai. But before these images, the following things will happen without the user knowing:
- The first 64kb of the DS's firmware is overwritten by junk data, preventing the unit from starting up.
- The first sectors of a inserted GBA Movie Player gets erased, but can be recovered.
- The firmware for both the SuperCard and the XG/Neo get erased. This cannot be recovered.
Plus, a secondth modified version was uploaded named "DS Owata" in 2009 with some altered text, with the rom pretending to be Dragon Quest IX. After the erasing job is done, some text and hentai will be displayed on the screen:
Some of the text is also different in DS Taihen and DS Owata:
Taihen:
DS taihen v1.0 This is a small hentai slideshow. Just sit back and relax :) Wait several seconds to see the next picture.
Owata:
DS owata :) This is a DS owata :) slideshow. Just sit back and relax :) Wait several seconds to see the next picture.
When the user would turn the DS off and back on again, they will be greeted with a black screen.
Trojan.DSBrick.A (r0mloader.zip)
A day later, a more wildspread and more approperiate version was uploaded on multible IRC channels and a forum as well, named r0mloader.zip. The trojan pretended it was a tool that would "automatically patch your .nds roms uppon launch", but its functionality was the same as DS Taihen.
r0m loader for Nintendo DS It automatically patches the game during load. You can switch DS card / GBA cart save and save settings per game. Put the loader on a CF or SD card together with the NDS files. Start the loader and select the NDS to play! Enjoy. Currently supports: * Supercard * GBA Movie player Future support: * G6 * M3
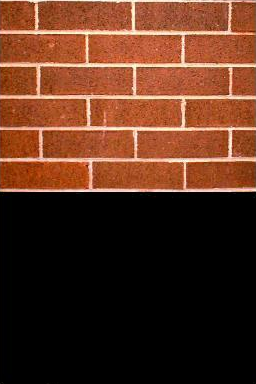
After the erasing job is done, an image of a brick wall is shown on the top screen, with no activity. Because this version of CrashMe was more wildspread, the news was covered on multible websites and forums, being mostly virus-alert sites, with a warning for people telling them to keep an eye out and to always get roms from trusted sources.
CrashMe (2011)
Another trojan popped up around 2011, found by a GBAtemp user known as osm70, with a message that he found it on a regular warez site, pretending to be Mario Party DS. The file size is 58,5MB.
Rom details
r0mloader.zip:
Filename: r0mloader.zip Contents: r0mloader.nds, r0mloader.txt NDS MD5 Hash: a959cfa514f4c7162a81421ee99d3356 NDS SHA1 Hash: 862e8e46a922d46244506a963519f18207d5b20f NDS CRC32 Hash: 1efb58ba NDS Filesize: 151 361 bytes
taihen.zip:
Filename: taihen.zip Contents: taihen.nds, taihen.txt NDS MD5 Hash: 8e7a3728759df265ca3a78553cf27bb8 NDS SHA1 Hash: Unknown? NDS CRC32 Hash: 08aa2d30 NDS Filesize: 548 673 bytes
DS Owata:
Unknown?
CrashMe (MPDS):
Filename: Unknown? NDS Filesize: 58 500 000 bytes
IRC Log(s)
Origin of r0mloader.zip:
23:46 @<xxx> 23:45 +<djPepse> <DarkFader> shall I make different version that's a supposedly loader? ;) 23:46 @<xxx> 23:46 +<djPepse> <DarkFader> http://akusho.xs4all.nl/temp/r0mloader.zip >:) 23:46 @<xxx> idiot 23:46 @<xxx> kille som har gjort en "rom loader" till nintendo ds 23:46 @<xxx> som inte alls laddar rommar 23:46 @<xxx> utan istället kvaddar firmwaren 23:46 @<xxx> så ens nintendo ds går sönder ;/
DarkFader's apology (2005)
After everything went down, DarkFader has appologised for his actions and behaviour as he clears everything up, including some recovery tools for the bricked consoles and flashcarts.
I want to say sorry to everyone out there. I should have realized the impact. Not just few DS'es that were hurt, but all the damn media and whatnot. I cannot really justify my actions. It was also very selfish to draw some attention, which I tend to do in odd ways. It caused some harm to some non-targetted and targetted people owning a DS with non-Nintendo-approved hardware. And that is a terrible thing to do. Even more so with the reputation I had in the DS homebrew scene that now completely abandoned me. I do not have clear reasons and I can't blaim the little headache I had at the time. I just had to realize the idea I had after seeing the PSP variant of a bricker. The files do not come with any form of name/signature of me, a thing I would do if it could be trusted. I won't release any more of this crap for DS and I don't think parts of this trojan or the idea itself will emerge in future homebrew releases. The point is probably clear. Do not run any form of untrusted code that just suddenly appears without any name. If you only use official Nintendo games, there is absolutely nothing to worry about. Untrusted code includes ROM loaders and that sort of stuff. It's probably not a very good reason since it has been proven before. I can tell that the negative feedback is far greater than the positive ones. I received one donation of $6.66 and I'm not proud of it. One news site completely ignores the r0mloader version and reasoning behind it. grrrrr. Another common mistake: A TROJAN IS NOT A VIRUS! That means that it does not propagate on its own. And thus non-intrusive. The trojan was released in two forms: Trojan.DSBrick.A, 151361 bytes, md5sum a959cfa514f4c7162a81421ee99d3356, r0mloader.nds Version A was intended for the so called ROM-pirates. Hence the name of the filename and description. It was anonymously posted to just a few IRC channels and one forum. Elsewhere, it was known that is was a trojan. After doing its thing, it shows a picture of a brick wall. Apropriate to the situation. Trojan.DSBrick.B, 548673 bytes, md5sum 8e7a3728759df265ca3a78553cf27bb8, taihen.nds Version B was not really released into public and should rarely be seen. It was only directly released in a closed IRC channel with prior notice of what it did and a comment that might have triggered some (less evil than me) persons to pass it along. After doing its thing, it cycles through five attractive drawings. I cannot control the propagation of the files or the names it might be disguised as. Ok, on to the more technical details: The trojan _tries_ (but not definately succeeds) to: * Erase DS firmware. Practically the first 64 KBytes are write-protected and thus is recoverable when the FlashMe firmware was installed. * Erase first few sectors of CompactFlash card inside GBA movieplayer. You can try to sort out your data sectors if you really want something back. * Erase GBA movieplayer firmware. Fairly easy to fix using flashmp utility. * Erase Supercard firmware. A fix is currently being worked on. * Erase/lock XG/Neo flash card. Seems it was forgotten to be mentioned in r0mloader.txt. If you have a legal use for these functions like testing recovery tools, you're welcome. Here are some fixing utilities and links: ppflash.zip - Contains info, sourcecode and binary to flash the fail-safe loader also contained in FlashMe using a parallel port connection. Some soldering skills are required to perform this operation. Don't worry about voiding your warranty because you already have according to the DS manuals. FlashMe - The page to get FlashMe. You can't survive without it. flashmp.zip - Firmware flasher for GBA Movie Player. Supports writing to Supercard, but the included firmware IS NOT WORKING probably because of a bad firmware dump! If you have an original firmware version and Flash Advance Linker, let me know. Probably more to come. You can detect DSbrick by using DSbrick.signature and the utility grep: grep -F -U -f DSbrick.signature FileToBeTested.nds A good way to prevent malicious firmware access is to keep a record of known ARM7 binaries. This could be incorporated into ndstool.
References
- A video of Trojan.DSBrick.A
- A video of Trojan.DSBrick.B (NSFW warning)
- CrashMe on Nintendo 3DS (Another unknown variant known as "Firmware Programmer")
- Archived wiki article from PocketHeaven
- Gamespot covering DarkFader's appology
- GBAtemp staff "Another World" covers the Mario Party DS bricker
- Original link to r0mloader.zip (dead link)
- Original link to taihen.zip (dead link)